Get hacked. Become secure.

Our Mission
We are a Florida-born cybersecurity firm dedicated to protecting businesses from today’s most sophisticated threats. Our mission is simple: secure your business and safeguard your growth.

Penetration Testing (Ethical Hacking) & Code Review Audits
By working with Swiz Security, you can become rest assured that your business is made secure from hackers and other malicious adversaries on the Internet.

1 on 1 Security Planning & Audit Assistance
Become SOC2 compliant with our assistance.

Video Coaching Sessions
Our experienced security professionals conduct critical educational sessions via video conferencing, ensuring a seamless and engaging experience.
“I have known the owner of Swiz Security for over 15 years, his character is impeccable. He is very intelligent, possesses an excellent work ethic and is an outstanding young man.“
– Greg Agresta Executive Vice President & Director of Commercial Administration at WesBanco
Start your journey
Experience Peace of Mind Through Security by Choosing Swiz Security.
Schedule your free consultation and find out how Swiz Security can help you secure your business.
Courses
Premium courses coming soon!!
Reverse Engineering
Reverse engineering is the art of deconstructing software to uncover its design, logic, and hidden mechanics.
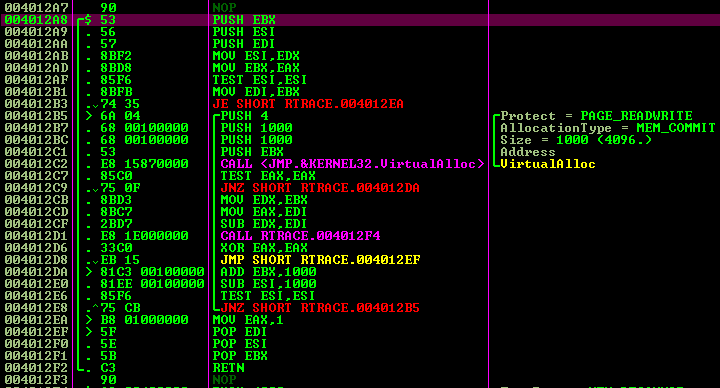
Logical Port Enumeration
This blog uncovers logical port enumeration. This is the process of mapping out which network services are accessible on a system. It reveals the attack surface.

Binary Exploitation
Binary exploitation is the practice of manipulating flaws in compiled programs to alter their intended behavior at the lowest level of software.

Windows Shellcode Development
and events
Jul 23, 2025 — 09:00pm EST
›
Cybercast After Dark (EP. 2): Shellcode and Exploit Development w/Jacob Swinsinski
Explore the latest trends, techniques, and tools transforming the world of Windows Security Research.
May 4, 2024
›
Mastering Android Security Research: A Guide for the Modern Security Researcher
A Guide for the Modern Security Researcher by Hahna Latonick Jacob Swinsinski

May 4, 2024
›
Becoming a Certified Android Exploit Developer (Exam Time Lapse)
Navigating the complexities of modern mobile security.
Jun 6, 2024 — 03:00pm EST
›
All Things Cybersecurity
All Things Cybersecurity.
Apr 18, 2024 — 08:00pm EST
›
Thirsty Thursdays Live Show
Learn about breaking into the world of cyber security and learn about Android Hacking!

Secure your life and workplace with creativity and innovation.
Florida Born. Globally Trusted.
- Code Reviews: We go beyond automated scans with meticulous, hands-on reviews to identify vulnerabilities at the source.
- Penetration Testing: Our expert team simulates real-world attacks to uncover weaknesses before adversaries do, delivering actionable insights and clear remediation paths.
- SOC 2 Compliance: We guide you through every step of the compliance journey, aligning your security posture with industry standards to earn customer trust and open new markets.
From startups to enterprises, our tailored services empower organizations to innovate securely and meet compliance goals with certainty.
Global reach. Relentless protection.






